Overview
Stigg’s integration with Auth0 natively connects Auth0’s identity management with Stigg’s entitlement enforcement capabilities. Instead of manually building custom integration logic, developers can leverage the integration to seamlessly authenticate users and enforce feature access based on entitlements. The integration ensures that when users authenticate, they’re granted access to the correct set of features in Stigg, enabling the application to function according to their plan limits.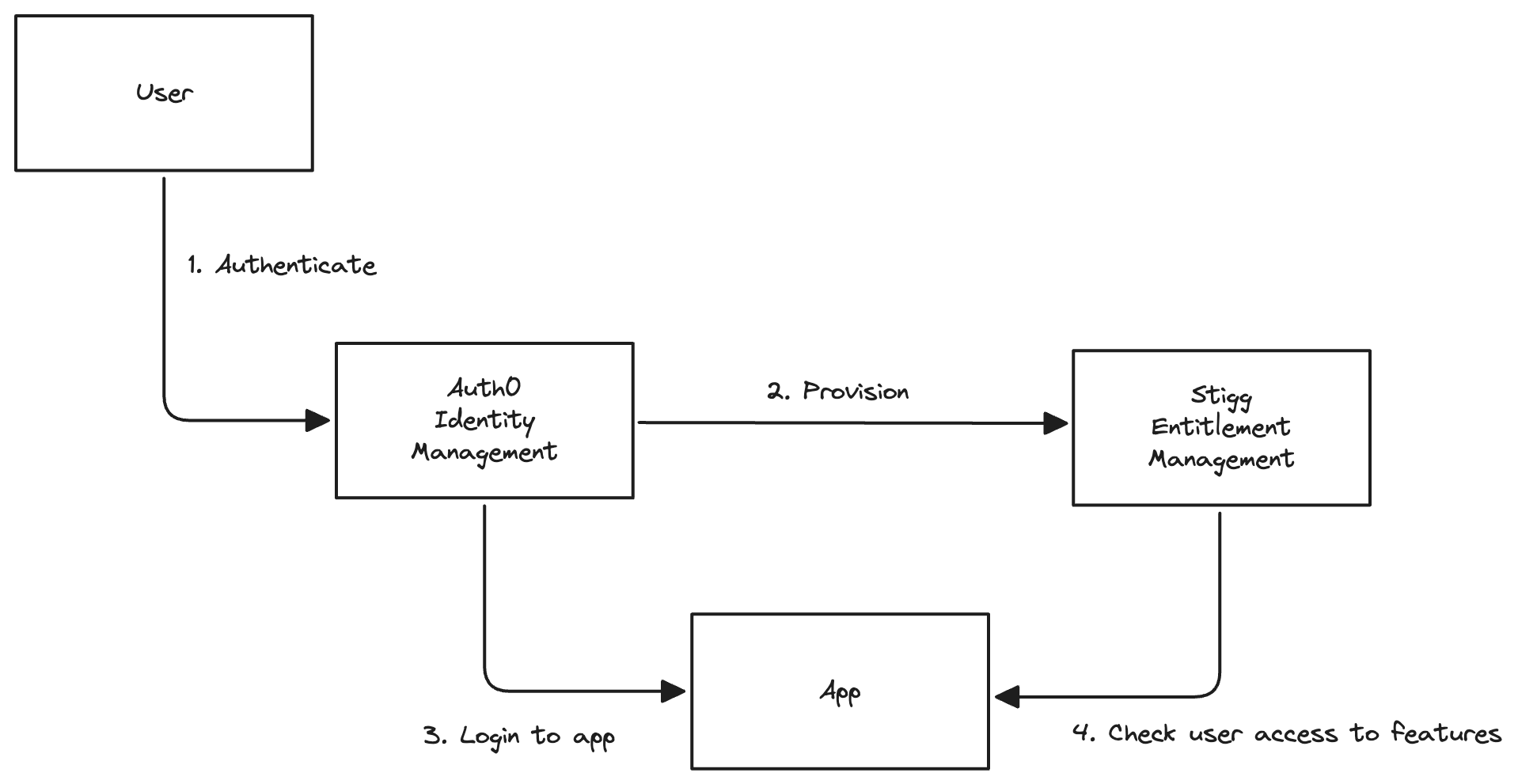
Common use-cases
This integration addresses several use cases that streamline app development and improve end-user experience.Automatic provisioning
In Stigg, a customer can represent either an individual user or an organization, handling both B2B and B2C flows. With Auth0 and Stigg you can easily provision subscriptions for both B2B customers and B2C users when they are onboarded by configuring product-level customer journeys, like assigning new customers with a default free plan, or starting a trial for a paid plan are possible in no-code.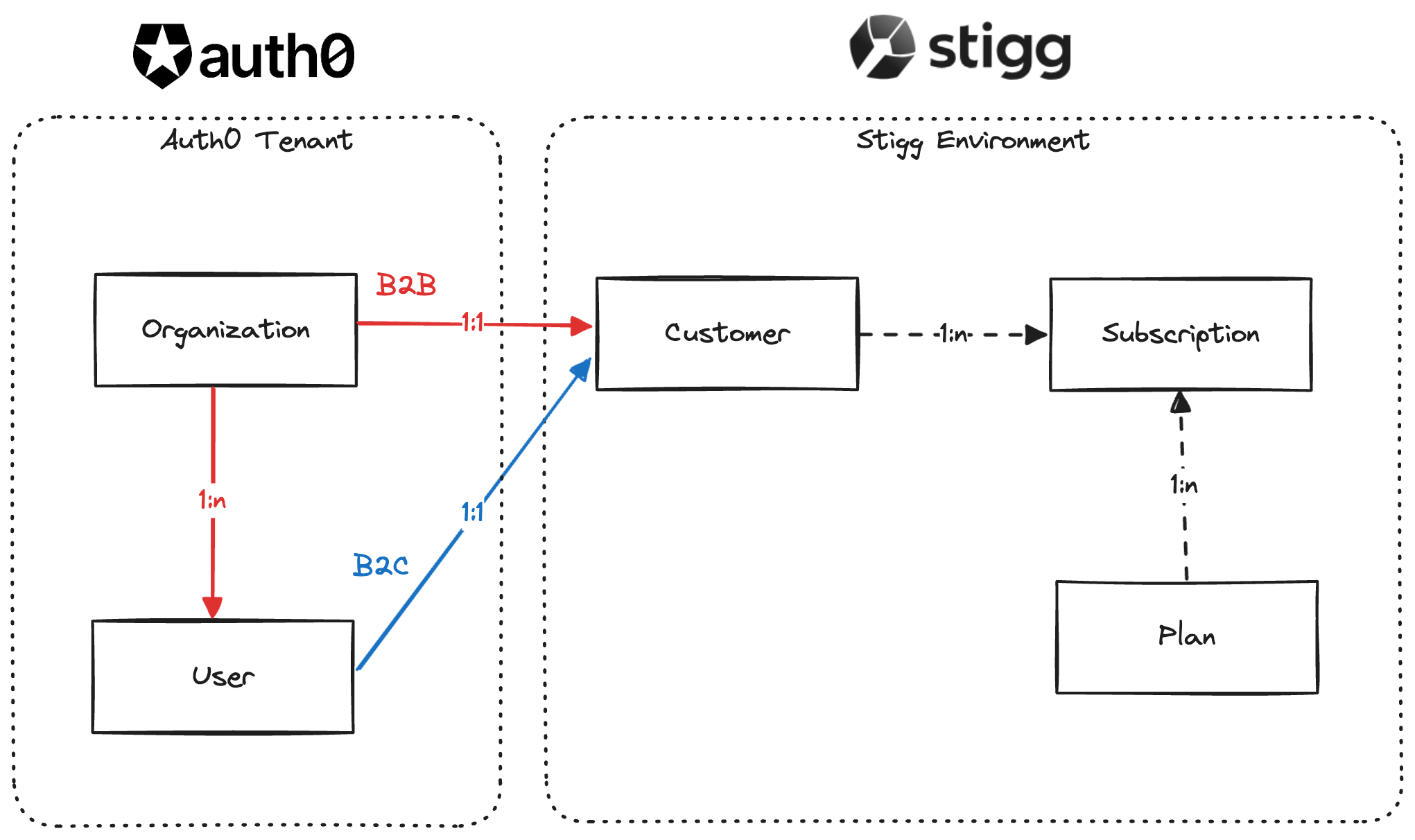
Automatic active users metering
For B2B companies, tracking active users helps measure product adoption and growth. This integration automatically tracks active users during the login process, making it easy to implement usage-based billing models like pricing per Monthly Active Users (MAU). This is especially helpful for self-service plans, where customers typically pay based on their actual usage instead of a fixed number of licensed seats.Enforcing user limits
Tracking active users can also help enforce seat limits. The system can ensure that the number of active users stays within the limits of their agreement, which is ideal for fixed-seat contracts. This helps both vendors and customers stay aligned with the terms of their plans.Gate identity related features
While not part of the integration, using Auth0 and Stigg allows entitlement enforcement for typical paid features like Single Sign-On (SSO) or System for Cross-domain Identity Management (SCIM). You can use Stigg to check if users have access to configure a feature, and then use Auth0 to set it up. This makes it easy to offer tiered features that scale with customer needs, and create upsell opportunities for larger customers.Setting up the integration
This integration connects an environment in Stigg to your Auth0 tenant by creating:- One Action in your Auth0 tenant’s Post Login flow to handle Stigg customer provisioning from Auth0 users and organizations, and send login events to Stigg.
- An “Active Users” metered feature in Stigg for tracking MAUs based on Auth0 logins.
Prerequisites
To begin integrating Auth0 into your Stigg project, there are a few requirements that you’ll need to set up before getting started:- A Stigg account with an environment that you would like to integrate with.
- A product in Stigg with a free plan or paid plan with a free trial.
- An Auth0 tenant - you can learn more about how to set one up here.
Set up the Stigg client in Auth0
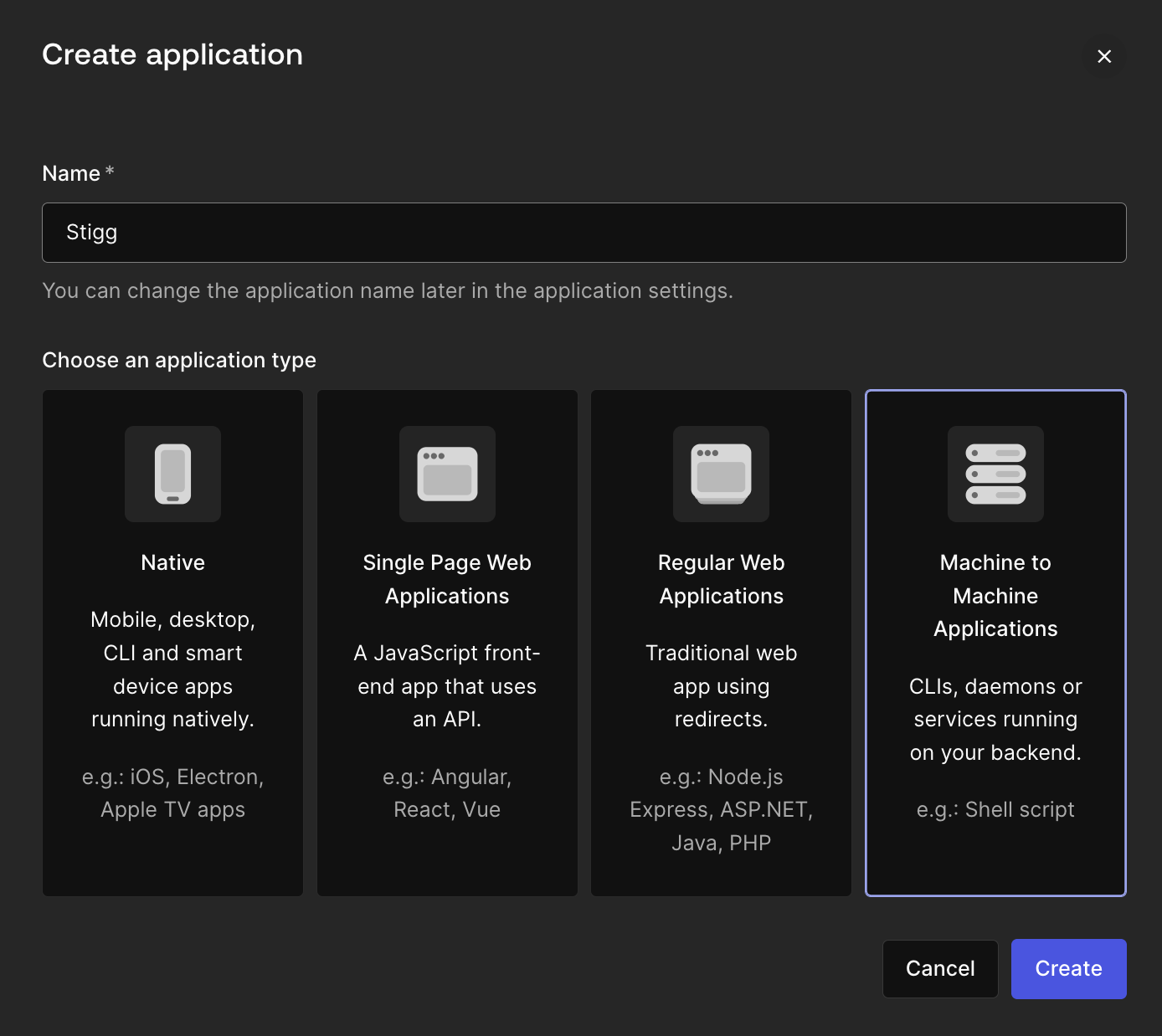
In Auth0, select the tenant that you’d like to integrated with Stigg. In the left navigation pane, under “Applications” select “Applications”.
- Application name - recommended: “Stigg”
- Application type - “Machine to Machine Applications”
-
Actions
- read:actions
- update:actions
- delete:actions
- create:actions
-
Triggers
- update:triggers
- read:triggers
-
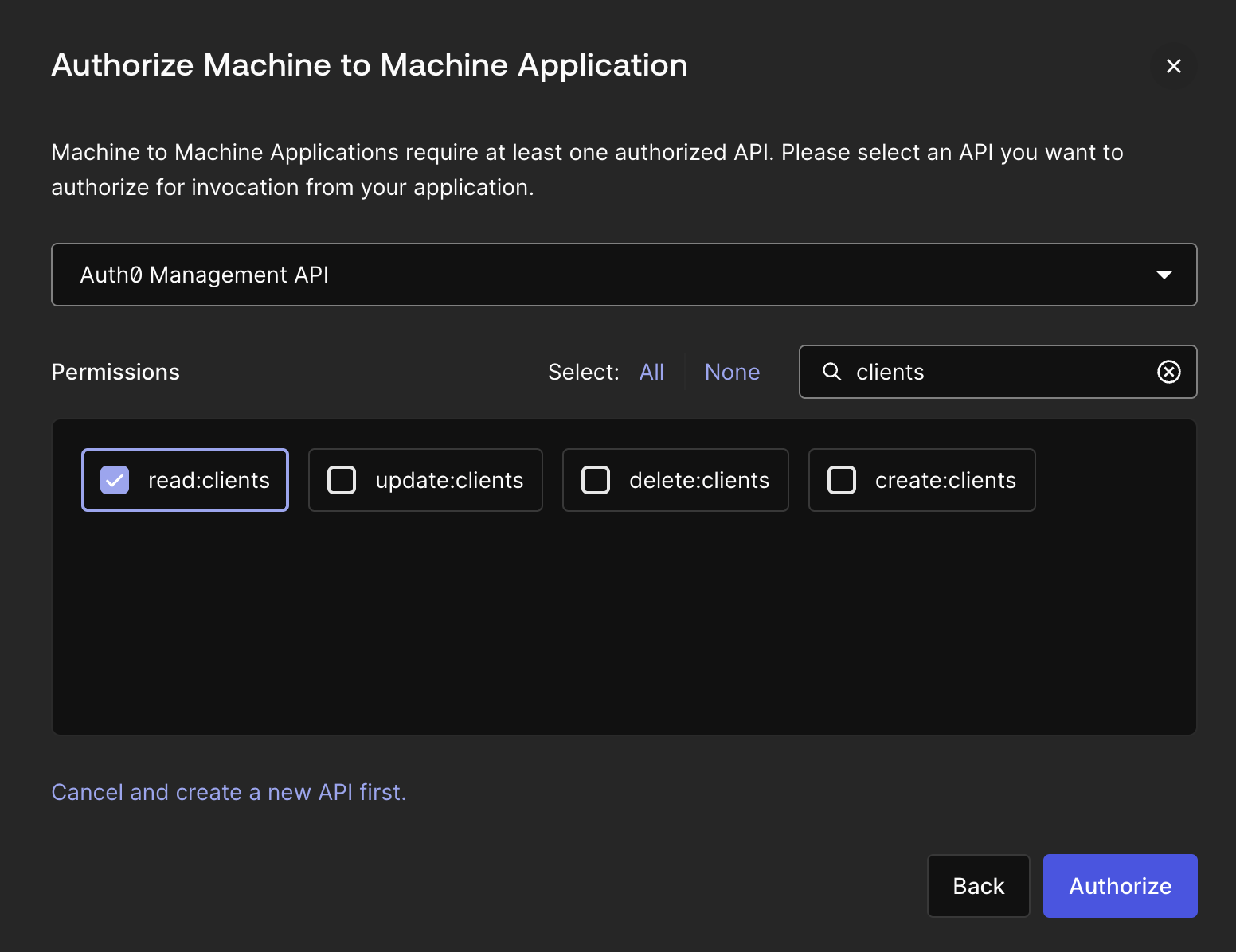
Clients
- read:clients
-
Organizations
- update:organizations
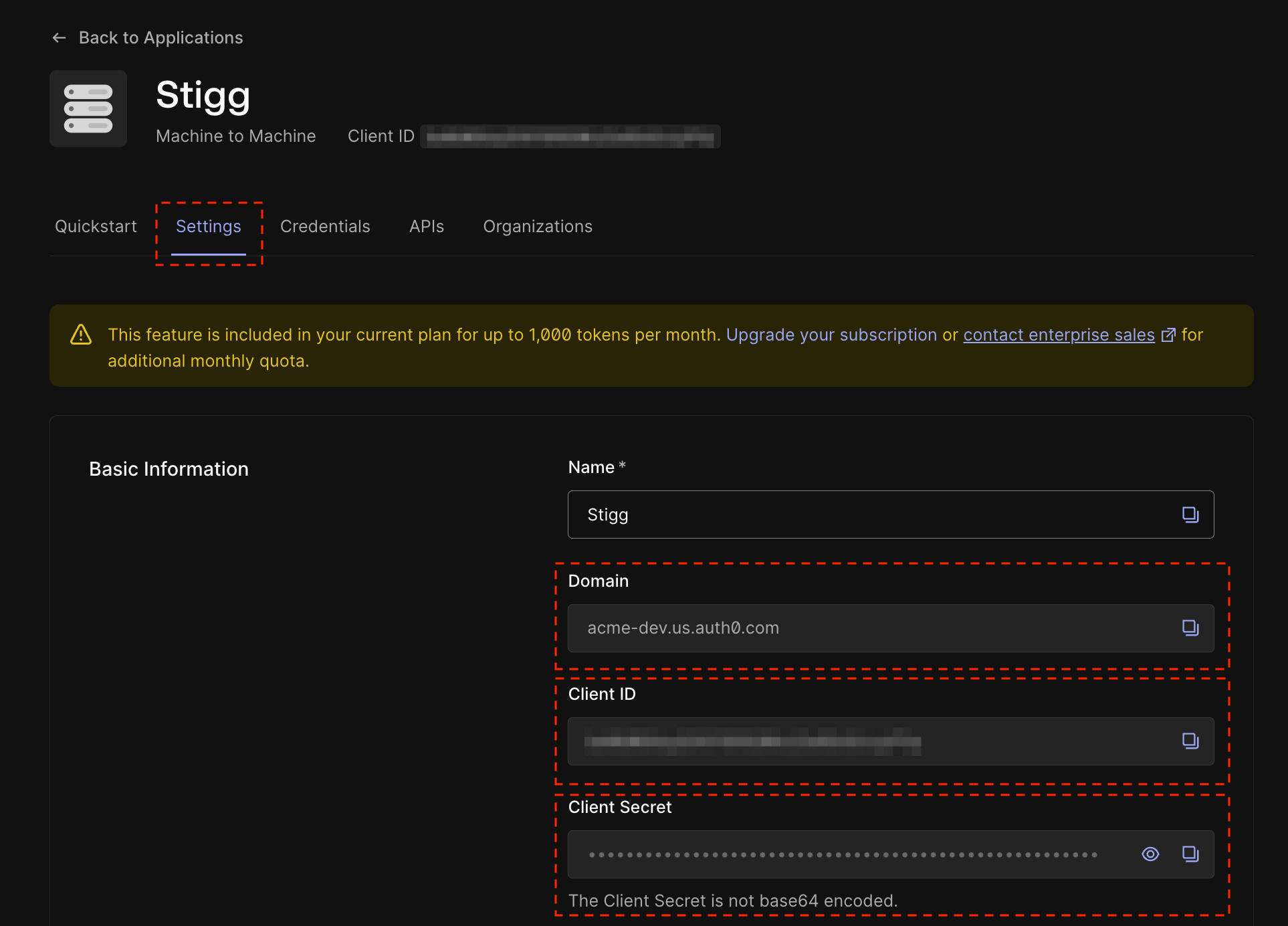
- Domain
- Client ID
- Client secret
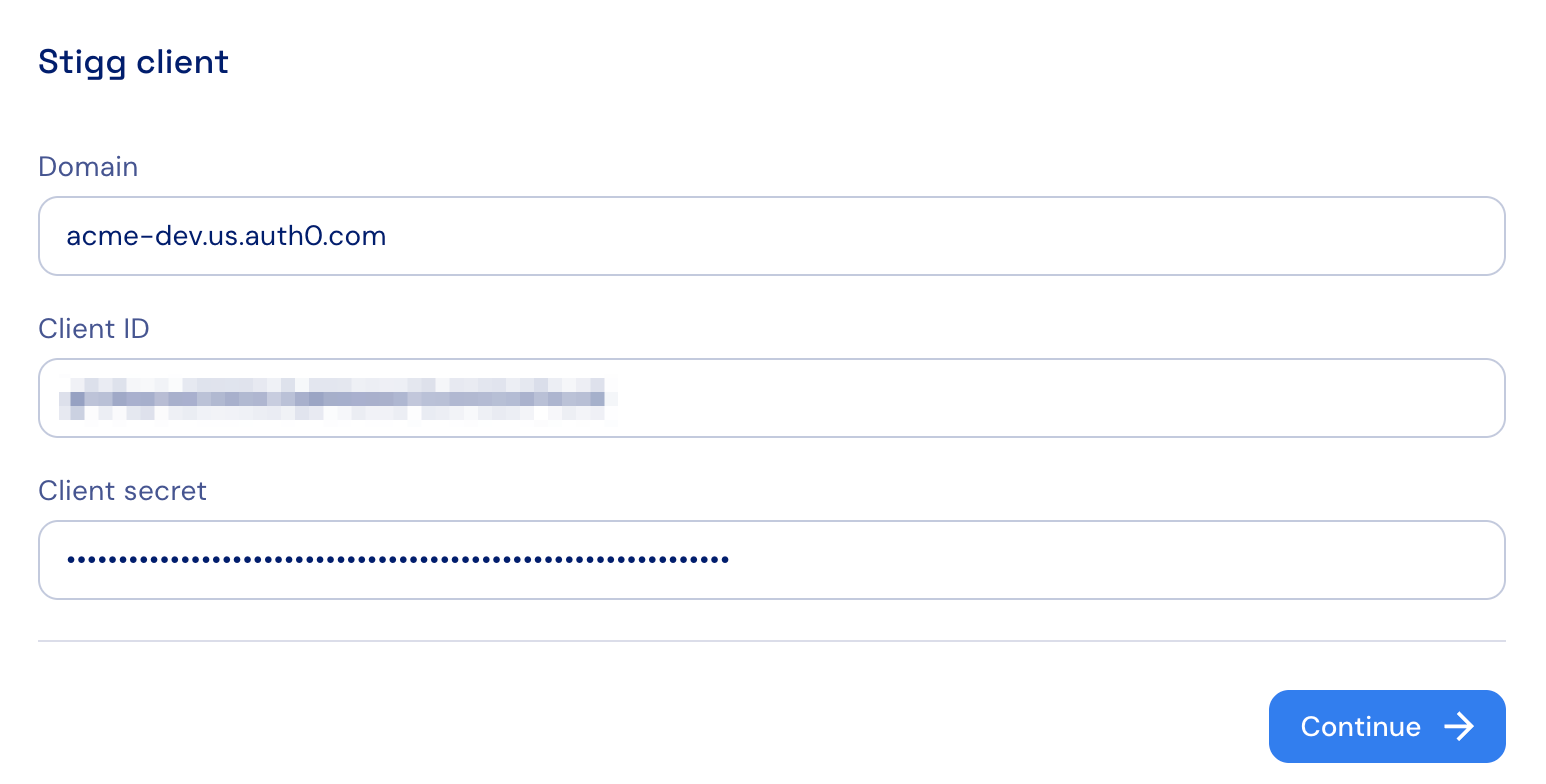
Connect Stigg to Auth0
In the Stigg app, navigate to the Integrations section and click on the Auth0 tile. Click “Continue” to proceed to the “Stigg client” section. Enter the details of the Machine-to-Machine application that you created in the previous step:- Domain
- Client ID
- Client secret
When the connection setup is successful, Stigg will automatically create a new “Active Users” metered feature, which will be used for tracking successful login in Auth0.
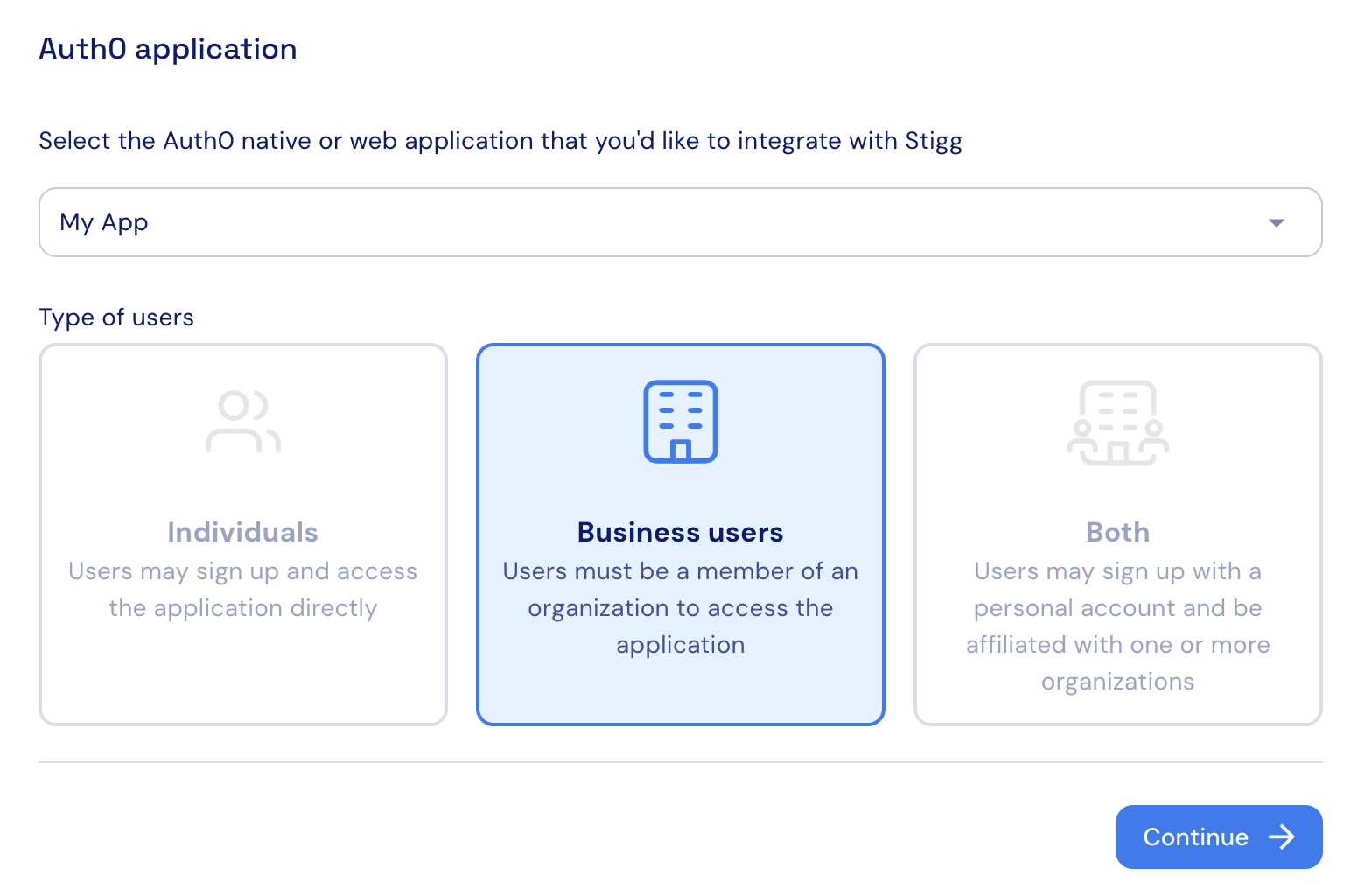
Select the Auth0 application
Select the Auth0 native or web application that you’d like to integrate with Stigg. Upon selection, Stigg will also reflect the types of users that are allowed to authenticate with the application:- Individuals (B2C)
- Business users (B2B)
- Both
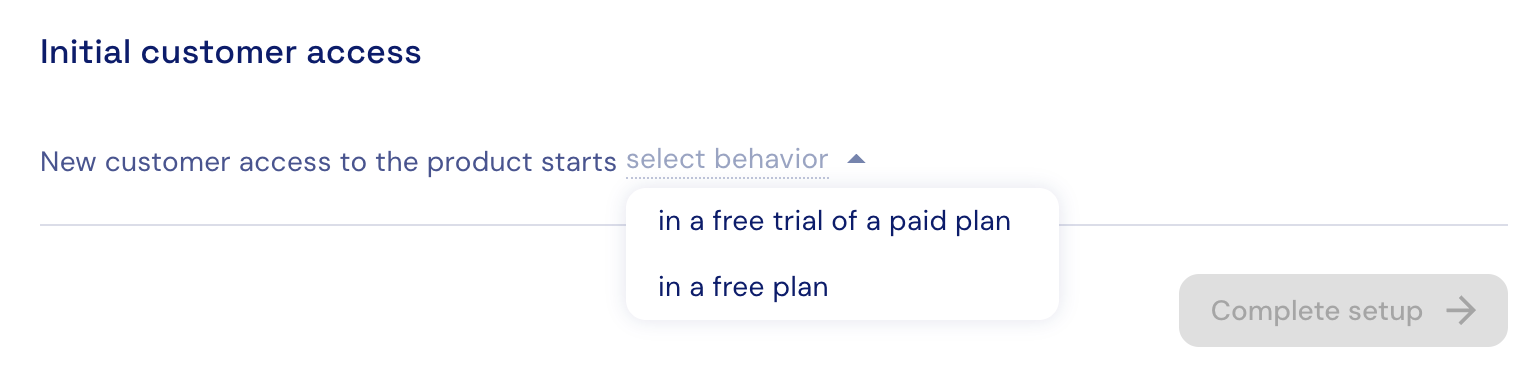
Define the initial customer access
Enforcement and billing according to customer access requires a customer and subscription to be created in Stigg. Luckily, as part the native integration between Stigg and Auth0, Stigg can automatically provision customers and subscriptions upon successful login according to Auth0 app type:- When the Auth0 app is configured for “Individuals” (B2C), every logged in user as a customer.
- When the Auth0 app is configured for “Business users” (B2B), the user’s organization is considered as a customer.
- When the Auth0 app is configured “Both” (B2C + B2B), a customer and subscription will be created in Stigg depending on how they logged in - as an individual (1) or business user (2).
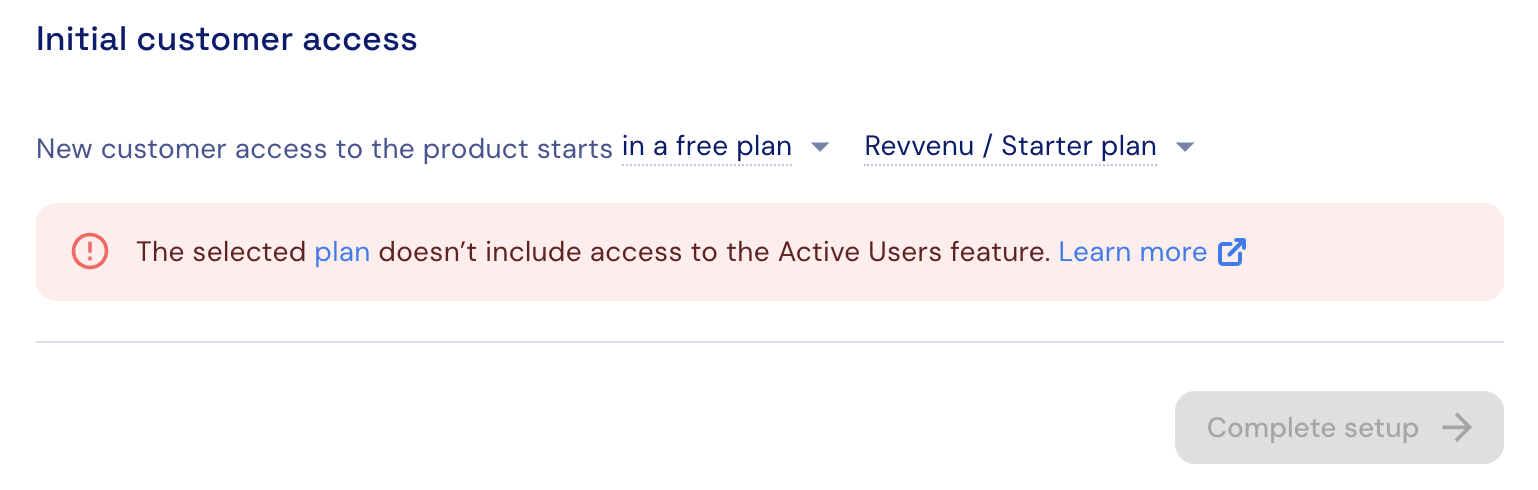
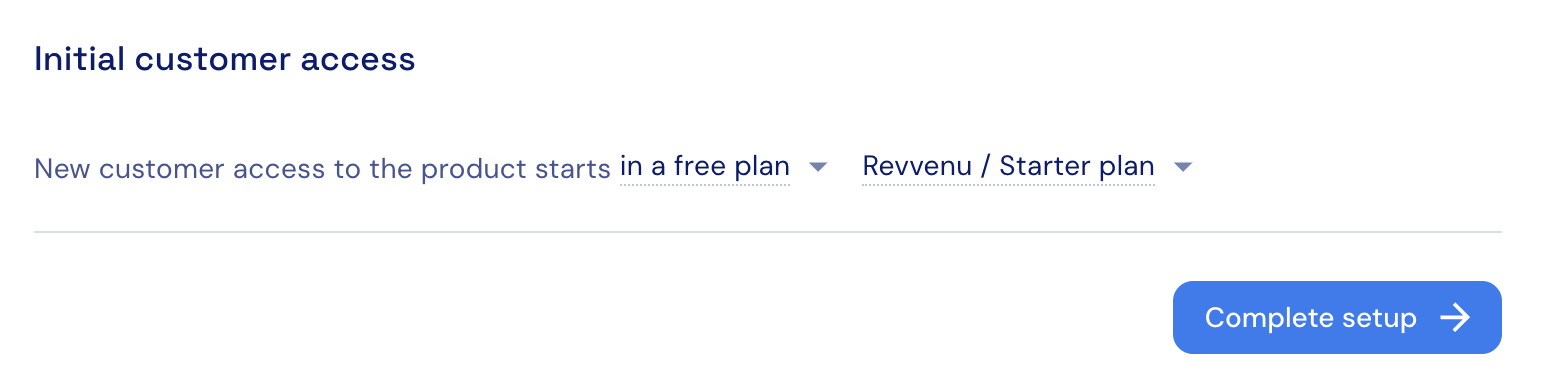
When the selected Auth0 app type is intended for both individuals (B2C) and business users (B2B), it’s possible to select a separate default plan for each type of user.
Auth0 Action
As part of the integration process, Stigg creates an action in the Auth0 tenant at the end of the Post Login flow. The action handles both customer and subscription provisioning, usage metering, and enforcement of active users’ limits belonging to an organization. It operates in the Post Login flow of the Auth0 tenant and automates critical aspects of user management. When a user logs in the action provisions a customer in Stigg. If the user has logged into an organization, the customer will be created and associated with the organization of the user (B2B), otherwise the customer will be created and associated with the user (B2C). The customer subscription is automatically provisioned according to the configuration in Stigg. This step eliminates manual subscription plan assignment, ensuring users start with the right level of access. The action also meters and enforces the limit of active users belonging to an organization. For example, you can easily limit the number of MAUs in a free plan, and charge customers based on the number of MAUs in a paid plan. If the MAU limit is reached, Auth0 restricts new user logins, allowing for a straightforward upgrade path.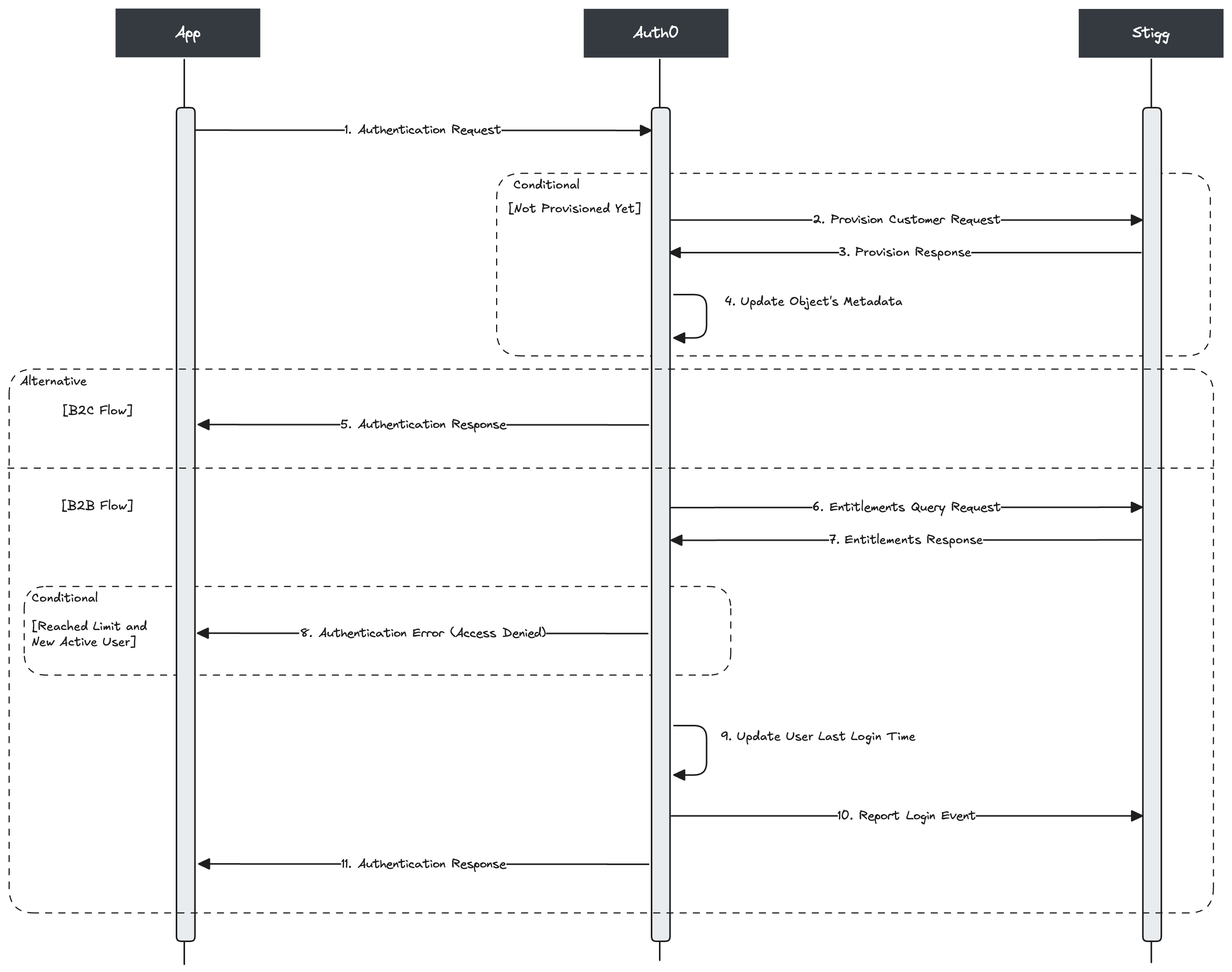
- An app makes an authentication request to the Auth0 server, triggering the Auth0 Post-Login Action
- (Conditional) If the customer associated with the user (B2C) or organization (B2B) has not yet been provisioned based on the metadata of the Auth0 object, the Auth0 Action sends a request to Stigg to provision the customer. Note: Depending on the type of login, the customer ID is mapped to either Auth0’s organization ID (B2B) or user ID (B2C).
- Stigg provisions the customer and sends a response back to the Auth0 Action.
- The Auth0 Action updates the metadata of the Auth0 object to indicate that the customer has been provisioned.
- (Conditional) If the login flow is B2C, the action stops execution and allows the login flow to continue.
- The Auth0 Action sends an entitlement query request to Stigg.
- Stigg returns the entitlements to the Auth0 Action.
- (Conditional) If the active users’ entitlement usage exceeds the limit, and the user’s last login time is not within the current usage reset period (i.e. it is a new active user), halt the login flow and return an “Access Denied” error message.
- The Auth0 Action updates the user’s last login time in Auth0.
- The Auth0 Action reports the login event to Stigg.
- The action allows the login flow to continue.
